Building Cyber Resiliency In Cell And Gene Therapy Manufacturing
By Sanjay Srivastava, Global Cell and Gene Therapy Lead; Mike Van Chau, OT Security Senior Manager; and Stas Verberkt, North America Life Sciences Security Lead at Accenture

To ensure patient access to life-saving therapies, resilient business processes are a critical priority for Cell and Gene Therapy (CGT) companies. Resilience against cyber-attacks is a critical component of this overall strategy. Given CGT’s time-sensitive operations and vulnerable patient populations, any operational impact could have potentially disastrous patient impacts. Furthermore, the intellectual property (IP) for first-in-class therapies used by CGT companies is a prime target for cyber criminals.
CGT companies typically execute over 50 vein-to-vein manufacturing processes which utilize over 25 applications. Typically, half of these applications are managed internally, and the other half are managed by third parties, including Contract Manufacturing Organizations (CMOs). Critical manufacturing applications commonly include Manufacturing Execution Systems (MES) and Industrial Control Systems (ICS) often referred to as Operational Technology (OT).
Additionally, Business systems have become integral to manufacturing operations. For example, document management systems and quality management systems are put in place to ensure good practice (GxP) quality controls and regulatory requirements are being met. Even office applications such as Microsoft Outlook, Teams, and SharePoint have become critical to support CGT manufacturing operations. In many CGT environments, such critical business applications are managed by cloud service providers or third parties.
Understanding the trends in the biopharmaceutical market and how they impact resilience against cybersecurity threats provides critical context to define a roadmap for further maturing cyber resiliency. This understanding provides organizations with a way to measure their cybersecurity maturity against their peers and prioritize key gaps. A successful journey to increase cyber resiliency and reduce cybersecurity risk requires transformations across people, process, and technology. Furthermore, given the criticality of CGT manufacturing facilities, the cybersecurity strategy guiding this journey should be set in the boardroom and not just on the shop floor.
In a previous article, we proposed how CGT manufacturers can use a CGT-asset driven approach to understand their cybersecurity risk and how to best prioritize investments in building an end-to-end cyber resilient process. Once manufacturers’ cybersecurity teams gain an understanding of how the IT systems affect business processes and associated risks, they can ultimately understand how these systems impact patients. With this knowledge, CGT cybersecurity teams can start to build thoughtful cyber resilient structures and networks for the end-to-end CGT manufacturing processes. To establish cyber resiliency of CGT manufacturing processes, cybersecurity teams typically follow three distinct maturity stages:
- Building a strong cybersecurity foundation
- Integrating cybersecurity operations
- Proactive cyber defense and threat intelligence
Nevertheless, many cybersecurity teams face a series of challenges in effectively building their cyber resiliency strategies following this approach. From talent shortages to heightened threats, cybersecurity teams face a new series of challenges they must adapt to for providing access to life-saving medicines.
By keeping these challenges in mind, cybersecurity teams can proactively prepare for their cyber resiliency journey.
Current Challenges for CGT Companies
As CGT companies are increasingly investing in cyber resiliency of their manufacturing facilities, it is important to review some key challenges we are seeing in the biopharmaceutical industry and how they impact cybersecurity requirements.
1. Global Talent Shortages
As many CGT companies are looking to scale their operations, the rising demand for highly specialized talent has resulted in serious talent shortage for these organizations. The same dynamic holds for the cyber resilience efforts these companies have, given that OT security subject matter experts are scarce as well. These are experienced professionals with manufacturing experience and familiarity with the latest OT security technologies and controls, as well as experience integrating these technologies into existing manufacturing process operations.
2. Innovation, Automation and OT/IT Convergence
To sustain the growing demand for cell and gene therapies in the market, CGT manufacturers are turning to automation and other innovations to enable new operational capabilities and efficiencies. These innovations are enabled by increased integration between facilities and OT/IT networks. For example, facilities increasingly leverage centralized enterprise resource planning (ERP), management systems, and analytics to manage operations. Other examples of innovation and automation include assisted reality on the manufacturing floor for new operator training, or various CGT manufacturers leveraging video-based quality verifications for overseeing manufacturing quality control processes. As CGT manufacturers continue to innovate and the boundaries between OT and IT environments continue to converge, the attack surface significantly increases resulting in a growing susceptibility of these environments to cyber-attacks.
In addition, many life sciences organizations still have legacy architectures in their manufacturing environments that increase their exposure to cybersecurity threats. While many organizations have made investments to legacy architectures, cybersecurity risks remain and become more prevalent as a result of the convergence between OT and IT operations. To illustrate these cybersecurity implications, Figure 1 shows how manufacturing networks have typically evolved over the past 20-years, and how this has impacted cyber resilience.
As shown in Figure 1, most manufacturing facilities had a flat network architecture with business and manufacturing systems on the same network in the early 2000s. This means that any malware outbreak can rapidly spread from a single system to the entire network. By 2010, a portion of biopharmaceutical companies started separating their IT and OT manufacturing networks using a so-called demilitarized zone (DMZ) to restrict traffic flows between these environments, thereby making it easier to contain a cybersecurity event to either the IT or OT environment. Over the past 4 years, many biopharmaceutical companies started to further segment their IT and OT networks. By having critical assets deployed into separate zones, cyber threats such as ransomware can be contained within a single network segment and prevented from moving laterally throughout the network.
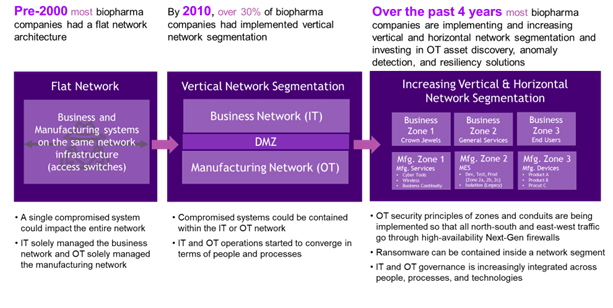
Figure 1. Illustrative 20-year history of network cybersecurity evolution in biopharma industry
3. Growth through Mergers and Acquisitions
As there continues to be significant growth by acquisition in the CGT market and the wider biopharmaceutical industry, this often results in organizations with multiple manufacturing facilities that have varying levels of cyber resilience and maturity. This is commonly reflected in differences in architecture, disjointed processes, and operational silos. CGT companies should leverage a robust set of integration policies, reference architectures, and procedures to help smooth the transition and synergize the tools and processes in a timely manner and reduce the attack surface and cyber risks of these facilities. To achieve a better return on any investment in cyber resilience, standardization should be a core part of the cybersecurity strategy.
Even CGT manufacturers with a high level of cybersecurity maturity struggle with end-to-end visibility and asset management as it relates to their acquisitions. Often, CGT manufacturing facilities being acquired have a lower level of cybersecurity capability maturity than the parent organizations, which needs to be overcome to increase overall cyber resilience.
4. Rising Regulatory Requirements
On top of the existing regulatory frameworks that are in place for CGT manufacturers, cybersecurity requirements are being more and more formalized. As a result, biopharmaceutical companies are increasingly subject to audits, quality control, and additional technical control requirements to comply with these regulations. While this isn’t a new phenomenon, CGT processes are subject to these same regulations, which can be harder to comply with considering some of the legacy software and hardware systems laboratories and manufacturing processes utilize. As CGT rises in popularity and more patients are turning to CGT companies for treatment, cyber resiliency in these factories will begin to shift from a strict compliance focus and transform to using to newer technologies and more secure architectures. All of this comes on top of other regulatory factors that CGT manufacturers need to consider, such as data privacy regulations.
5. Heightened Cybersecurity Threats
As attackers utilize more sophisticated techniques and malicious code becomes easier to purchase on the Dark Web, Cybersecurity threats will continue to increase. This is especially true for biopharmaceutical companies located in conflict zones and the United States. Since most biopharmaceutical companies are on a middle-to-lower end of the maturity spectrum, cyber resiliency becomes even more important when considering business continuity planning (BCP) and disaster recovery (DR) for CGT manufacturing systems and processes. Without consistent testing of policies, processes, and technologies, biopharma companies may fall behind, leaving them even more vulnerable to the rising wave of attackers. Conversely, as companies race to pick up the latest technologies to help circumvent these attacks and transform their environments, they also leave themselves open to attacks from unknown elements due to a lack of skills and expertise in utilizing these tools and operationalizing their key capabilities and integrations.
The CGT Cyber Resilience Program Journey
As cybersecurity teams think about building their CGT cyber resiliency, these aforementioned challenges need to be kept in mind. The journey to build a CGT cyber resilience program can take several years to accomplish and teams must stay vigilant on their potential challenges to implement solutions. To support cybersecurity teams, we help our clients with their OT cyber resilience capability maturity roadmap across four major phases that include ways to execute short- and long-term risk reduction strategies and tactical plans. Figure 2 provides an overview of the natural progression of cybersecurity maturity capabilities on the journey to building an effective OT cyber resilience program.
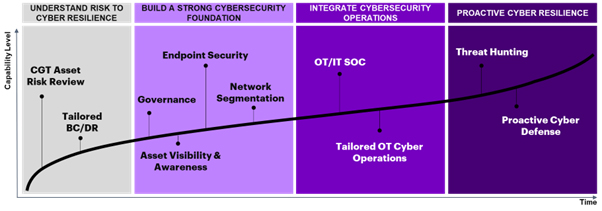
Figure 2. Key capabilities for maturing an OT security program through cyber resilience initiatives
1. Understanding risk to cyber resilience
The first step in risk management is understanding the assets that are part of the organization as well as those assets managed by third parties and the level of criticality those assets have in day-to-day manufacturing operations. Once these risks are understood, then the appropriate plans and investments can be made in ensuring business continuity and disaster recovery capabilities achieve the desired level of risk reduction. In a previous article, we describe how CGT manufacturers can use a CGT-asset driven approach to understand cybersecurity risk and prioritize investments to address this first step in the maturity journey.
2. Building a strong cybersecurity foundation
To build a cyber resilient OT network, each network must have 4 foundational aspects: a well-defined governance structure, complete asset visibility, robust security controls for endpoint systems (e.g., computers, manufacturing equipment, any devices that connects to the network), and a securely designed segmented network. With these aspects, cyber security teams will best set themselves up for success in integrating systems across the network. It is recommended that organizations leverage the ISA/IEC 62443 standard for Industrial Automation and Control Systems Security as they are building out these cybersecurity architectures.
Prior to building any cyber resilient network architecture, any effective manufacturing cyber resilience program must first have strong foundations in governance. As the IT and OT worlds converge, it’s important to have a well-defined and documented OT governance model to define roles and responsibilities of the team. This way everyone understands what components they are responsible for and understands how their role fits within the larger cyber resiliency program.
Furthermore, the entire governance model must have clear visibility into all assets within the manufacturing network. Without this, further cybersecurity protections are inherently less effective, as they cannot be targeted to protect the most critical assets. CGT companies will often find themselves addressing this in conjunction with quality management requirements that ensure current configurations are maintained and changes in the manufacturing environment are controlled, as both require a complete and accurate inventory and change control processes for IT and OT systems.
In parallel to establishing clear governance and asset visibility capabilities, foundational cybersecurity controls should be established and include endpoint protection and network segmentation. Cyber resilience initiatives for the endpoints often include next-gen anti-virus or endpoint detection and response (EDR) solutions that are tailored for manufacturing environments. In addition, it is recommended to leverage application micro-segmentation technology to isolate and protect critical applications, and “allow listing” to control which systems are allowed to communicate with each other.
Network and application segmentation are critical components of cyber resilient manufacturing facilities, as they make it significantly harder for malware to spread laterally. Network and application segmentation helps reduce the “blast radius” of a ransomware compromise to a single network segment vs the entire network, and thus reduce the impact and recovery time of such an incident. However, performing network segmentation requires the complete asset visibility, accurate asset inventory information, and up-to-date network architecture diagrams (high-level and low-level) to plan the transformation. Additionally, network segmentation efforts often require significant investments in time to complete the architectural changes to the environment. While an organization goes through this time-intensive network transformation for a manufacturing facility, the team can leverage endpoint controls such as application micro-segmentation and “allow listing” which can be more quickly and easily deployed to reduce risks during the transformation period.
3. Integrating cybersecurity operations
Once the cybersecurity foundation is established for a manufacturing site, organizations should continue to build out their cybersecurity operations. This should include integrating event log sources from OT systems into the security operations center (SOC) to enable cybersecurity monitoring in these manufacturing environments. As most SOCs are geared towards monitoring IT environments, this also requires developing security monitoring use cases that are tailored to manufacturing environments. Threat intelligence feeds tailored to OT environments and the life sciences industry can provide insights into the relevant cybersecurity threats for more targeted security monitoring. It is also recommended to further tailor and test operational cybersecurity processes specific to the OT environment, such as crisis management and incident response playbooks, to be ready for the worst-case scenario.
Currently, most organizations are at a point in their cyber resilience program journey where they need to integrate their IT and OT cybersecurity operations to enable a single unified cyber detection and response capability. This requires technical integrations between IT and OT (cybersecurity) applications such as OT visibility and monitoring solutions, IT service management (ITSM) solutions, security incident and event management (SIEM) platforms and security orchestration automation and response (SOAR) solutions. Integration between these technologies with provide the SOC visibility across the entire enterprise, regardless of whether it is an IT or manufacturing environment, to detect and respond to cybersecurity threats and understand overall the cybersecurity trends affecting the organization.
4. Proactive cyber defense and threat intelligence
Once a CGT manufacturer has established strong integrated cybersecurity operations, it is recommended to pivot towards proactive cyber defense capabilities. This will allow the organization to reduce the time to respond and contain cybersecurity events by leveraging automation and analytical capabilities such as artificial intelligence (AI). Proactive cyber defense requires well defined incident response processes that address both IT and OT business continuity and recovery capabilities. In addition, leveraging threat intelligence that is focused on specific threats to manufacturing and other OT environments as well as tailored to the biopharmaceutical industry helps to deploy limited resources to spend time on the most likely threats and identify proactive ways to address those threats.
How to Define Your Next Steps In Building Cyber Resiliency
Ultimately, the CGT therapy space is rapidly evolving and expanding. To ensure patients’ safety and data remains secure, cyber resiliency needs to keep pace. As biopharma companies seek to increase and secure their CGT manufacturing footprint, a comprehensive cyber resilience program focused on critical risks to business operations is paramount for patient access. These programs require multi-faceted defenses that address people, process, and technology-related threats to increase the overall resilience and protect the end-to-end value chain. With the cyber resiliency journey described in this article, CGT manufacturers are now armed with the blueprint on how to strategically build these protection efforts. To kickstart this cyber resiliency journey, we recommend organizations initially focus their efforts on:
1. Creating An Asset-Driven Strategy
As you begin to design your strong cybersecurity foundation, ensure you tailor the CGT cyber resilience journey according to your assets’ specific business risks, as previously described. Your tailored cyber resiliency strategy should include a roadmap for securing your end-to-end CGT value chain by identifying both short-term and long-term objectives. By having a tailored strategy and roadmap, organizations can decide how to allocate and prioritize resources to address both short-term, high-impact objectives and long-term, strategic goals.
2. Finding Quick Wins
Depending upon the current state of your cyber resiliency, the cyber resiliency journey may take multiple years to redesign networks, integrate and operationalize cybersecurity technologies. As you identify appropriate redesigns within your tailored strategy’s long-term objectives, don’t forget to identify short-term objectives. Identify the “low-hanging” fruit to help secure facilities and processes that may have high business impacts but low implementation complexity. These may include things like tightening controls on firewalls, increasing endpoints controls, or uplifting physical security at facilities.
3. Remaining Flexible
The regulatory environment and threat landscape of CGT therapies continue to change and tighten; biopharmaceutical companies need to regularly review and adapt their cyber resilience strategy to address the latest shifts in regulations and threats.
BIOGRAPHIES
Sanjay Srivastava, Global Cell and Gene Therapy Lead
Sanjay has a broad and deep expertise in the underpinning science and business challenges in developing and launching both in-vivo and ex-vivo cell & gene therapies. He directs his C> team at Accenture, who has global expertise in R&D, supply chain, manufacturing, and commercial operations.
Mike Van Chau, OT Cybersecurity Senior Manager
Mike’s experience spans numerous market sectors including pharmaceutical, oil & gas, chemical, electric utilities, food & beverage, military, and aerospace organizations. Mike is passionate about protecting critical infrastructure through industrial control systems (ICS) cybersecurity programs using top effective controls and solutions tailored to the environment’s risk profile.
Stas Verberkt, North America Life Sciences Security Lead
Stas is a senior manager with Accenture Security specialized in the biopharmaceutical industry. He works closely with Accenture’s biopharmaceutical clients to help define and execute cybersecurity strategies to protect their critical business operations and data against cybersecurity threats. Stas has over a decade of experience in cybersecurity consulting and received a Master of Science specialized in cybersecurity from the University of Twente. He lives in New York City with his wife and their two sons.
