Securing Cell and Gene Therapies Access for Patients
By Lena Walton, Cell and Gene Therapy Management Consultant; Stas Verberkt, Life Sciences Security Senior Manager; Sanjay Srivastava, Managing Director, Cell & Gene therapy lead, and Praveen Govindarajan at Accenture
Cell and Gene therapies (CGTs) are driving the wave of therapeutic innovation in the life sciences industry. CGTs have not only changed the game for modern medicine, but they have also dramatically changed the case for cyber resiliency. In traditional pharmaceutical manufacturing, life sciences companies were able to build a strategic stockpile of critical drugs for the worst-case scenarios. For cell and gene therapies, this is not always the case, as they are typically tailored to patients which restricts efforts to build inventory. In addition, patient demand far exceeds the supply, and any major disruption could result in patients not receiving potentially lifesaving treatments. As CGT patients are usually in the latter stage of treatment where many traditional paths have been exhausted, disruptions can have devastating impacts. Furthermore, pharmaceutical industry’s intellectual property (IP) for first-in-class therapies are prime targets for cybercrime. Thus, CGT manufacturers should be focused on the resiliency of processes, systems, and data within their vein-to-vein value chain in order to protect against cyber-attacks.
Traditionally, cyber resiliency efforts are driven by business teams and cybersecurity teams in silos, which leads to suboptimal results. In our experience, a blended team of business and cybersecurity resources result in accelerated value realization for the companies. To have a cyber resilient end-to-end process, we propose a CGT-asset driven approach that enables manufacturers to:
- Develop strong business continuity plans (BCP) for high business impact processes – including manual workarounds -- in case an IT/OT (information technology/operational technology) system were to fail due to a cyber-attack (as enforced by the FDA’s 21 CFR 11.10(c) and the EMA’s Annex 11 Section 16); and
- Ensure IT/OT environments are resilient against cyber-attacks through risk-based deployment of security controls to ensure persistent and secure availability of processes, systems, and data.
With these two methods established, CGT manufacturers can breathe easier knowing their therapies and patients are protected against potential cyber-attacks or system disruptions.
A Case Study Highlighting Importance of Cyber Resiliency
Given the time-sensitive nature of most CGT therapies, any meaningful BCP must consider each therapy’s end-to-end process, which usually spans from patient onboarding to treatment infusion. Particularly, autologous cell therapies add increasing logistical complication due to the fact that the final drug product’s raw material is the patients’ cell. Any breakdown or disruption along these processes can potentially cause significant delays or even complete loss of patient batches or treatments. For example, in autologous CAR-T manufacturing, the manufacturing execution system (MES) that supports manufacturing environments typically must be recovered within a few hours in case of an outage to avoid loss of patient cells. If patient cells are lost, manufacturers have to completely restart the entire process and may even require fragile, weak, and immunocompromised patients to undergo another round of apheresis to collect more cells.
To complicate things further, MES is not the only system that manufacturers depend on. MES is one example of a critical component within an entire technology stack infrastructure that must be effectively orchestrated to bring life-saving therapies to patients. Other examples include, but are not limited to, LIMs systems to support cell integrity, ERP system to support raw material supply, logistics partners’ software systems to coordinate shipment, cell ordering systems to schedule and place orders. Therefore, companies must not only ensure that these systems have technology controls to guarantee its secure availability during a cybersecurity incident, but also the business process team must work in parallel to establish procedures that allow the manufacturing process to move forward if any system fails.
Asset-Driven Approach to Business Continuity Plans
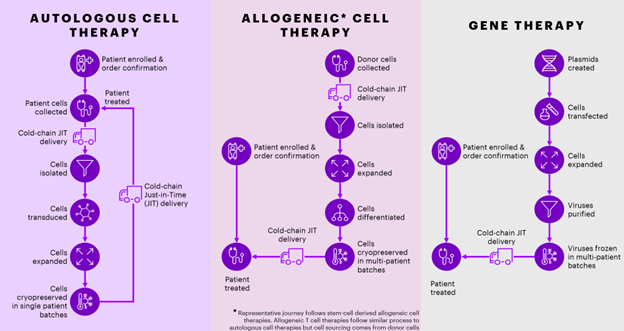
To ensure CGT therapies can reach patients in the event of an IT/OT system outage, it’s important to establish clear business continuity plans (BCP) that are specific to each CGT asset. The figure below gives a depiction of the similarities and differences of high-level, business-critical process steps for each CGT therapy. Depending on your CGT therapy, your processes might be different, and it’s critical to understand each therapy’s unique processes to have a strong BCP. Furthermore, each cell type and viral vector type will have its own process sensitivity. For example, consider the differences between autologous immune cell therapies and allogeneic stem cell-derived therapies. Autologous cell therapies are cell therapies derived from the patients’ cells while allogeneic cell therapies are derived from healthy donor cells. Therefore, if MES fails and loses one batch of an allogeneic cell therapy – yes there will be business impacts due to batch loss, but if backup donor batches are stored within the facility, the cell therapy can still be delivered to patients with minimal to no delays. Since allogeneic cell therapies and gene therapies do not require each patient’s sample, their resiliency to manufacturing delays depend upon the inventory levels of their raw materials and overall batch size. Therefore, BCPs must account for these nuances.
When to Think about Cyber Resiliency Efforts
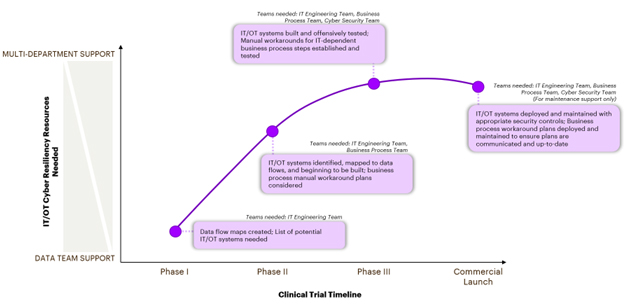
CGT manufacturers should begin to think about cyber resiliency and business workaround plans as they scale their manufacturing in clinical trials. In Phase I, most CGT manufacturers are supporting efforts to build a standardized process of manufacturing. As you choose to invest in equipment and machinery, it is important to keep track of the data flows, system dependencies and interfaces, as well as seek to understand the relevant cybersecurity threats. This will ensure that as you scale, the processes, systems, data, and the IT/OT environments are built with cyber resiliency requirements embedded in the design.
By Phase II, the manufacturing processes are established, and should be focused on scaling, building any additional end-to-end architecture, and establishing a robust QC process. As manufacturing scales, companies tend to rely more upon IT/OT systems to automate processes. This is the phase when companies should actively plan and implement cyber resilient technology processes and tools. In addition, manual process workaround plans should be established each time a process needs an IT or OT system for process completion.
Thus, by Phase III, companies will have elevated their cyber defense and tested manual process workaround plans to enable a cyber resilient post commercial environment.
How to Establish to Cyber Resiliency in A Resource-Constrained Environment
We’ve discussed how CGT manufacturers can leverage risk-based thinking for cyber resiliency, but it’s also important to discuss how manufacturers should be planning and implementing cybersecurity controls involving technology (tools and systems), tech processes and site-supporting personnel (system teams). While it might be easy to say all end-to-end processes must be cyber resilient and have manual process workaround plans for crisis scenarios, organizations will most likely find it too resource-intensive to work on all relevant cyber resiliency efforts at the same time. This is not due to dependencies on different internal teams who also must be focused on commercial launch and commercial post-launch activities. Therefore, we propose an approach that assesses the business-processes within a CGT asset to identify key areas (processes and systems) of focus. Once key areas of focus have been identified, both cybersecurity teams and business process teams will need to work in parallel to build cyber resilient structures and business process manual workaround plans, respectively.
Map the Business Processes and Analyze Their Impacts
First, all business processes between “Enroll Patient” to “Patient Treated” should be mapped and clearly identified; this includes all ordering, manufacturing, scheduling, and QC processes. Once all necessary processes are identified, the next objective is to gain insight into how each process affects the business if it were to fail. For example, what are the business implications between failing to schedule drug product delivery on-time vs. failing to properly purify a gene therapy virus from host cells? We typically assess business criticality through a 5-pointed lens: Patient Safety, Brand Reputation, Financial Implications, Operational Impacts, and Regulatory Considerations. Placing your business processes on a spectrum according to this business criticality score gives one dimension as to which business processes need immediate and robust cyber resiliency plans. Process failures with high business impacts should be identified by business process owners and prioritized as processes of interest that need clear BCPs.
Understand the IT and OT Landscape
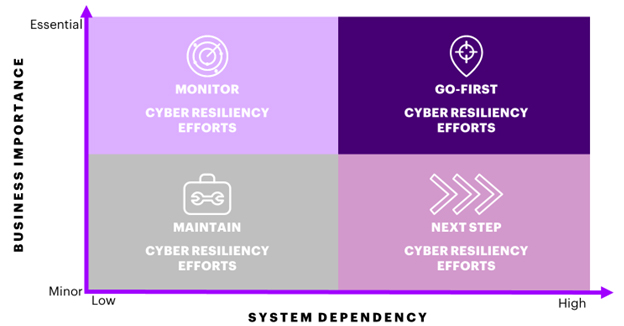
In addition, one should gain visibility into the supporting systems, applications, devices, and data that enables these steps within the end-to-end process. This will provide clearer insight into how overall criticality of the process translates into risk levels for the individual supporting technologies, and ultimately gives you a cyber resiliency prioritization framework. For example, long-term temperature-sensitive storage of the final CGT drug product is critically important to the CGT business due to the fact most storage containers contain more than one patient’s dose. If the temperature-monitoring/notification system is completely digital and cannot function without an IT/OT system, that is a business process that is a “Go First” priority for cyber resiliency efforts. As a “Go First” priority, this means both business process owners, system owners and cybersecurity teams should be immediately deployed to both build BCP with manual workaround plans and implement cyber resilient technology processes and systems, respectively. All business processes that exhibit high system dependence with minimal workaround plans should be either in your first or second wave of cyber resiliency work depending on business impact. Low system dependence processes should be continuously maintained and monitored in case their system dependencies change. Furthermore, good documentation practices and institutionalized capabilities are especially critical for those in this “maintain” quadrant, as these will help achieve robust processes with predictable outcomes. By gaining a fuller cyber risk picture, CGT manufacturers can adopt a more pointed cyber resiliency strategy that is focused on protecting the most critical processes and systems.
Conclusion
Cell and gene therapies are poised to disrupt the healthcare ecosystem. However, unlocking true potential while serving an increasing patient population, requires strategic planning to elevate the cyber resiliency posture. Rapid advancements in digital innovations across the value chain make it imperative to focus on establishing a solid cyber resilient foundation. Successful companies recognize the importance and are positioning comprehensive cybersecurity and cyber resiliency plans alongside their asset development lifecycle. CGT manufacturers that deprioritize cybersecurity efforts risk their ecosystem being vulnerable to cyber-attacks that can adversely impact their business and the patients they serve.
To plan a successful cyber resiliency program, we recommend the following steps:
- Start with mapping the value chain and identifying the high business impact processes
- Understand the enabling IT and OT environment along with their relevant threats and vulnerabilities
- Prioritize cyber resiliency investments based on the business impact of the processes and their respective IT/OT dependencies, to:
- Identify process targets for business continuity, and
- Deploy security controls to protect processes, systems and data proportionate to the underlying risk
Acknowledgement of contribution to this article: Juhi Ramireddi
Biographies:
Dr. Sanjay Srivastava, Managing Director, Cell & Gene therapy lead at Accenture. Sanjay has a broad and deep expertise in the underpinning science and business challenges in developing and launching both in-vivo and ex-vivo cell & gene therapies. He directs his C> team at Accenture, who has global expertise in R&D, supply chain, manufacturing, and commercial operations.
 Praveen is a Senior Manager in Accenture Strategy practice with specialized focus on Cell and gene therapies. Praveen has more than a decade of consulting experience advising clients in the areas of Manufacturing and Supply chain.
Praveen is a Senior Manager in Accenture Strategy practice with specialized focus on Cell and gene therapies. Praveen has more than a decade of consulting experience advising clients in the areas of Manufacturing and Supply chain.
