Protecting Cell And Gene Therapy R&D Against Cyber Threats
By Sanjay Srivastava, Global Cell and Gene Therapy Lead; Stas Verberkt, North America Life Sciences Security Lead; Lena Walton, Cell and Gene Therapy Consultant; Zach Grieco, Life Sciences Security Senior Manager; and Mike Van Chau, OT Security Senior Manager at Accenture

Over the past few years, the COVID-19 pandemic has upended the societal norms we have grown accustomed to in our everyday life. This impact reverberated through most work environments, and the drug development space was not spared.
Through collaboration, technology advances, and regulatory support, drug developers demonstrated that a typically decade-long process could be expedited to a single year. Although these timelines were spurred by extraordinary circumstances, it has fundamentally altered the drug development space. Since then, innovation across the pharmaceutical space has continued to occur at a breakneck speed, and the cell and gene world is setting the pace. Cell and gene therapies (CGTs) offer the potential to provide first-in-class medicines to patients with unmet medical needs. With this potential comes multiple factors that lead to an increase in the pace of drug development: a highly competitive market landscape, significant advances in technology, and accelerated regulatory timelines (e.g. FDA’s Fast Track, Breakthrough Therapy, and Regenerative Medicine Advanced Therapy designations). To keep pace with the CGT accelerated drug discovery, pharmaceutical companies need to ensure their scientific laboratories continue to fuel new innovations and remain protected from cyber-attacks that threaten to hinder drug development.
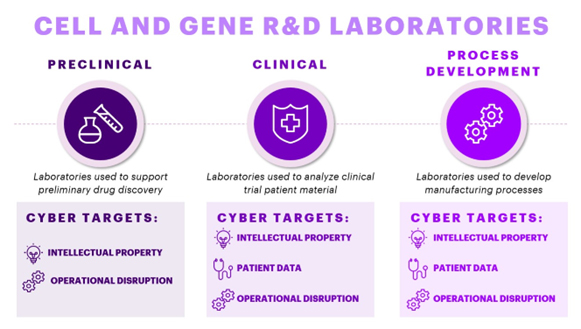
Fig 1. Types of R&D Labs within CGT companies & their Cyber Targets
In the cell and gene R&D world, we can classify scientific laboratory spaces into three broad categories: preclinical labs, clinical labs, and process development labs (Fig 1). Preclinical labs drive drug discovery prior to clinical trials, clinical labs support the analysis of clinical trial patient samples, and process development labs support the development of cell and gene therapy manufacturing. Each lab has its own needs and requirements with their own digital technologies that enable drug R&D. The data from these digital technologies drives CGT development. Across each lab type, intellectual property data typically becomes a primary target for cyber-attacks, but beyond this, CGTs offer their own unique cybersecurity risks. Many CGT therapies are personalized therapies – these drugs either require patient data or even patient material for manufacturing. Thus, many CGT labs not only contain highly sensitive intellectual property data but also patient data. Therefore, cybersecurity no longer becomes solely a threat to companies but also to patients themselves. As the stewards of this data, CGT developers must ensure proper data protection.
Nevertheless, accelerated innovation causes laboratories to become dynamic spaces with unique cyber resiliency challenges. If not managed appropriately, these characteristics may leave both IP and patient data at risk. To ensure proper data security, CGT developers must learn to identify the cyber security challenges of laboratory spaces and build appropriate cyber defenses.
Current Challenges Faced in R&D Laboratory Environments
CGT developers face two types of challenges when making their R&D environments resilient against cybersecurity threats. The initial set of challenges they face are the legacy issues faced across environments in the pharmaceutical industry, not just the CGT space. These primarily relate to pharmaceutical ways-of-working (e.g. outdated security architectures, cross-pharmaceutical ecosystem risks), and the fact that R&D spaces are incredibly dynamic environments. Secondly, CGT developers must confront a unique set of cybersecurity challenges within their market space. The CGT market is relatively nascent and extremely competitive, which can lead to insufficient cybersecurity preparedness making these companies highly susceptible to cybersecurity threats.
CGT Challenges
Unique Data Exchanges
Thus far, the CGT industry is almost entirely dependent on academia-driven innovation. Both large and small biopharmaceutical companies lead the development of CGT therapies, but both are highly reliant upon the initial PoC research performed in academic labs. Once cross-entity relationships are formed and contracts are signed, critical IP data transferring and sharing process must occur between academia and industry. These unique data exchanges create a unique vulnerability for IP as data moves between public and private sectors.
Evolving Critical Systems
Oftentimes many of the traditional lab systems are insufficient for CGT product development. To support R&D, CGT developers rely upon new or custom IT/OT systems to perform critical processes. These systems ultimately create new data types and new data pathways across non-traditional system relationships and functional boundaries. However due to these systems’ immaturity, most of them lack appropriate data privacy or security capabilities leading to cross-functional security threats. To exacerbate these challenges further, these novel systems have been created to perform critical process tasks, causing a significant reliance on their functionality and data.
Immature Cyber Defenses with Accelerated Timelines
Thus far, most CGT therapies are developed by smaller biopharmaceutical companies. Oftentimes these therapies are the first therapy in their pipelines. Additionally, many CGT therapies have been granted accelerated approval timelines, creating increased stress on R&D environments to accelerate innovation cycles. Due to their focus on building foundational infrastructure to support accelerated research & development, cybersecurity is frequently deprioritized. This subsequently means that highly targeted companies are woefully unprepared to defend themselves against cyber-attacks. Furthermore, if such companies are acquired by other organizations, more adequately prepared cyber security teams are suddenly faced with new unprotected assets that must be appropriately integrated into their existing environments and networks.
First-In-Class Threats
Within the CGT space, most CGT developers are attempting to achieve recognition from the fact first-in-class therapies provide reputational and commercial benefits. Due to these benefits, it also makes highly susceptible to cyber security threats. Cyber security threats may attempt to steal IP, delay the therapeutic development, or even steal/leak patient data. Therefore, CGT developers are more likely to be targets of cyber-attacks.
R&D Scientific Labs Challenges
Insufficient Visibility
To continuously drive and accelerate scientific discovery, R&D laboratories frequently change/update their equipment and computers within their environments. This often results in incomplete and outdated inventory of system assets due to the fact there are no regulatory requirements to keep track of assets within an R&D environment (unlike highly regulated, commercial manufacturing environments). Without an up-to-date IT/OT inventory, cyber security teams are limited in their visibility of what assets they need to protect and monitor against emerging security threats.
Cyber Hygiene Gaps
Not only do labs frequently change their IT/OT landscape, but they also often contain substantial legacy and unpatched systems due to vendor, resource, lifecycle, and regulatory constraints. Additionally, many companies do not prioritize cyber security within a lab environment, which can lead to gaps in adequate endpoint protection, exposing assets to security vulnerabilities. Ad hoc assets with limited security controls and threat monitoring are often brought into labs without regard to how they affect the lab’s cyber defenses.
Limited Network Segmentation
Some pharmaceutical organizations continue to have flat networks between the scientific labs and business environments. This means that there is no separation between these environments. In a flat network, all scientific lab assets are accessible through the same network as other non-lab devices. These networks provide increased damage in potential cyber-attacks due to sensitive asset data being accessible from anywhere on the internal network. Furthermore, when a flat network is breached, it is significantly easier for a cyber-attack to spread to additional assets on the same network, leading to an increased “blast radius”. These risks can be further compounded if there is also limited visibility and monitoring for security threats. Ultimately, flat networks become increasingly susceptible to cyber-attacks as organizations move towards digital labs, where the environments become further interconnected with the Cloud, external networks, and other assets outside of the labs.
Ecosystem Partner Risks
In most organizations, there are typically a substantial number of ecosystem partners with access to the scientific labs. This has further increased with the additional focus on remote work in the aftermath of the global pandemic. In most scientific labs, this includes, at a minimum, lab vendors, who may need remote and onsite access to maintain instruments and other assets, contract partners who support research or development activities, and contingent workers. Although these ecosystem partners are vital to the organization, the usage of third-party contractors and other external providers also causes increased exposure to security vulnerabilities. In fact, around 60% of recent cyber-attacks are associated with a third-party compromise.1 To mitigate these risks, it is important for organizations to have visibility of their ecosystem partners, the varying level of access they have, and the security controls in place to mitigate the risks.
Secure Science Lab Use Cases
Protecting these environments against cybersecurity threats requires tailored solutions that can be applied to diverse types of equipment and be scalable, all while minimizing impact to operations and keeping up with the pace of scientific innovation. A resilient lab has key elements of security-by-design which enable execution of the lab’s missions while reducing the “blast radius” of cybersecurity events. In this section, we’ll examine two typical use cases that CGT lab environments encounter as they set out to increase cyber resilience.
Use Case: Improving Operational Resilience
To improve operational resilience, we need a clear-eyed picture of requirements, culture, and capabilities. This begins with a thorough understanding of what devices and data are inside and outside the lab environment. Then the organization must strategically implement foundational controls that limit movement between these two zones. Even just these steps can dramatically reduce the impact of a cyber event like ransomware by creating barriers that stop the malware from crippling R&D lab systems and locking up critical data, sometimes permanently.
Resilience is achieved through a combination of network segmentation controls, application micro-segmentation and adherence to a network access strategy. A lab which has well-architected security will simultaneously provide secure access to data and equipment alike and feel frictionless to the users, while delivering secure and accelerated R&D activities that more effectively deliver on the mission.
Use Case: Secure Access to Scientific Lab Equipment
Keeping labs operating at speed requires on-demand access to equipment, data, and systems by a broad spectrum of employees, contractors, and third parties. Maintaining operational resilience means this on-demand access also needs to be secure access. As an example, nearly all CGT labs have equipment that requires maintenance and troubleshooting by off-site vendors or certified support contractors. Structuring the remote access for the specific job the support team needs to perform and abiding by ‘least privilege’ principles ensures that third-party access does not create risk to other systems or lab data. Effective management also reduces risk in an instance where credentials are compromised, by limiting impact. One of the primary keys to securing access to a R&D lab is to fully understand the identity, access, and equipment requirements specific to the environment. This typically includes data usage, equipment maintenance, operating tolerances, and sustained instrument performance, amongst others. Once the requirements of the lab are understood, the next step is integration of lab tools into a unified Identity and Access Management platform. Many organizations have already made these investments and leveraging what exists is a major accelerator and a key to success.
Long-term success relies on equal parts governance from cross-functional teams and clearly defined areas of ownership.
How to Get Started on Protecting CGT R&D Labs
Depending on the size of the organization, the transparency of its CGT R&D laboratories, and the timeframe for accelerated approval, the concept of building cyber resiliency in these spaces may seem daunting. Nevertheless, there are common first steps taken across the industry that can help support these efforts:
-
Take Inventory
The first step is to familiarize the cybersecurity team with the lab environments and systematically inventory the IT/OT assets of these labs. Depending on the organizations’ priorities, each organization will require its own unique approach of which labs and where to start. Commonly, CGT labs with the most sensitive data (e.g., patient data and IP) should be prioritized first. Fortunately, many IT teams within labs may already have a (partial) inventory list of all assets within the lab, but it will be necessary to perform due diligence to ensure these lists are up-to-date and accurate. Additionally, building a recurrent inventory checklist will be important to improve transparency and visibility in the long-term.
Another important factor to consider when inventorying the CGT R&D IT/OT environments is understanding all data sharing activities. Not only is it important to know what data is being produced from what systems, but the security team should understand if external data is needed to perform internal R&D activities or if that internal data needs to be shared with external parties (e.g. academia, contractors, etc.).
-
Assess Criticality
Once the IT/OT and data sharing infrastructure of a CGT lab has been inventoried, it’s important to understand the business critically of data types & if the lab produces any novel CGT data types. The security team will need to work together with business teams to appropriately assess the criticality of the data through a multi-factor lens. For example, let’s imagine a hypothetical system in a CGT R&D lab that produces proprietary data regarding the qualities of a cell therapy (“System A”). If this asset were to be compromised, it could expose pose a significant risk to IP. Understanding and working with the business on the criticality of each asset and data type always the cyber security team to start understanding which assets and data types must be prioritized.
-
Develop Risk & Business Priority-Based Strategy
With an inventoried list of assets & data and a deep understanding of which of these are most critical to business, it’s important to now prioritize the cyber security strategy. Most likely there will be assets with significant risks across different kinds of business priorities (e.g. operational risks, patient risks). Assets that span multiple different types of risks should be prioritized. As well, systems with the highest vulnerabilities should be further prioritized. For example, “System A” may have been a commonly used machine in research labs, however now it must be moved to the process development QA labs to support cell therapy manufacturing. Due to its novelty in manufacturing environments, System A does not yet have the mature cybersecurity capabilities that exists commonly on other manufacturing systems. Nevertheless, System A’s data is highly critical in QA release. Therefore, the cybersecurity team will need to align with the business to confirm their top priorities to ensure the risk-based cyber security strategy aligns with business needs.
About the Authors
Sanjay Srivastava, Global Cell and Gene Therapy Lead
Sanjay has a broad and deep expertise in the underpinning science and business challenges in developing and launching both in-vivo and ex-vivo cell & gene therapies. He directs his C> team at Accenture, who has global expertise in R&D, supply chain, manufacturing, and commercial operations.
Stas Verberkt, North America Life Sciences Security Lead
Stas is a senior manager with Accenture Security specialized in the biopharmaceutical industry. He works closely with Accenture’s biopharmaceutical clients to help define and execute cybersecurity strategies to protect their critical business operations and data against cybersecurity threats. Stas has over a decade of experience in cybersecurity consulting and received a Master of Science specialized in cybersecurity from the University of Twente. He lives in New York City with his wife and their two sons.
Lena Walton, Life Sciences Consultant
Lena is a Consultant within the Accenture Life Sciences R&D practice and specializes in Cell and Gene Therapies. She has both industry and consulting expertise in supporting biopharma companies develop, launch, and sustain Cell and Gene Therapy pipelines.
Zach Grieco, Cyber Resilience Senior Manager
Zach is a senior manager with Accenture Security specializing in security analytics. He has nearly two decades of experience developing data-driven security programs that measurably reduce risk and protect value. For the past three years Zach has focused on the development of senior executive and BoD metrics programs, empowering security organizations to more effectively communicate with their business counterparts. Zach lives in Virginia with his wife, three children, and many dogs.
Mike Van Chau, OT Cybersecurity Senior Manager
Mike’s experience spans numerous market sectors including pharmaceutical, oil & gas, chemical, electric utilities, food & beverage, military, and aerospace organizations. Mike is passionate about protecting critical infrastructure through industrial control systems (ICS) cybersecurity programs using top effective controls and solutions tailored to the environment’s risk profile.
12021 H2 Accenture Cyber Threat Intelligence Report - https://www.accenture.com/content/dam/accenture/final/a-com-migration/pdf/pdf-173/accenture-cyber-threat-intelligence-report-vol-2.pdf#zoom=40
